How the NSA Hacked Google and Yahoo!
Politics / Intelligence Agencies Oct 31, 2013 - 10:30 AM GMTBy: Mike_Shedlock
 In response to NSA Breaks Into Secure Communication Links of Google and Yahoo I received a few comments worth exploring.
In response to NSA Breaks Into Secure Communication Links of Google and Yahoo I received a few comments worth exploring.
Reader "Fury" commented "True encryption using the RSA algorithm is unbreakable today. No way can the NSA break the prime number encryption that is used, I don't care how many supercomputers they have."
A knowledgeable friend commented "The secure parts are impenetrable by computer technology. A break-in is impossible unless Google let them in or the NSA somehow got the encryption key. The latter would require human agents."
The article I linked to above came from an October 30 article in the Washington Post. Here is the chart in question.
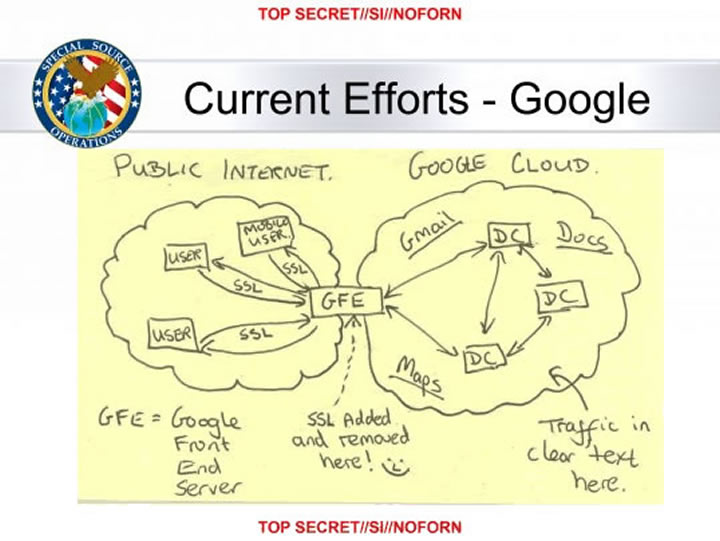
Man in the Middle
Mainstream media is nearly always late to these stories, and so was I. The answer to how the NSA hacked Google and Yahoo! comes from Schneier on Security a "blog covering security and security technology".
With thanks to reader "marvinmartian" for the link, please consider Bruce Schneier's September 13 post New NSA Leak Shows MITM Attacks Against Major Internet Services.
The Brazilian television show "Fantastico" exposed an NSA training presentation that discusses how the agency runs man-in-the-middle attacks on the Internet. The point of the story was that the NSA engages in economic espionage against Petrobras, the Brazilian giant oil company, but I'm more interested in the tactical details.
The video on the webpage [NSA Documents Show United States Spied Brazilian Oil Giant] is long, and includes what I assume is a dramatization of an NSA classroom, but a few screen shots are important. The pages from the training presentation describe how the NSA's MITM attack works:
However, in some cases GCHQ and the NSA appear to have taken a more aggressive and controversial route -- on at least one occasion bypassing the need to approach Google directly by performing a man-in-the-middle attack to impersonate Google security certificates. One document published by Fantastico, apparently taken from an NSA presentation that also contains some GCHQ slides, describes "how the attack was done" to apparently snoop on SSL traffic. The document illustrates with a diagram how one of the agencies appears to have hacked into a target's Internet router and covertly redirected targeted Google traffic using a fake security certificate so it could intercept the information in unencrypted format.
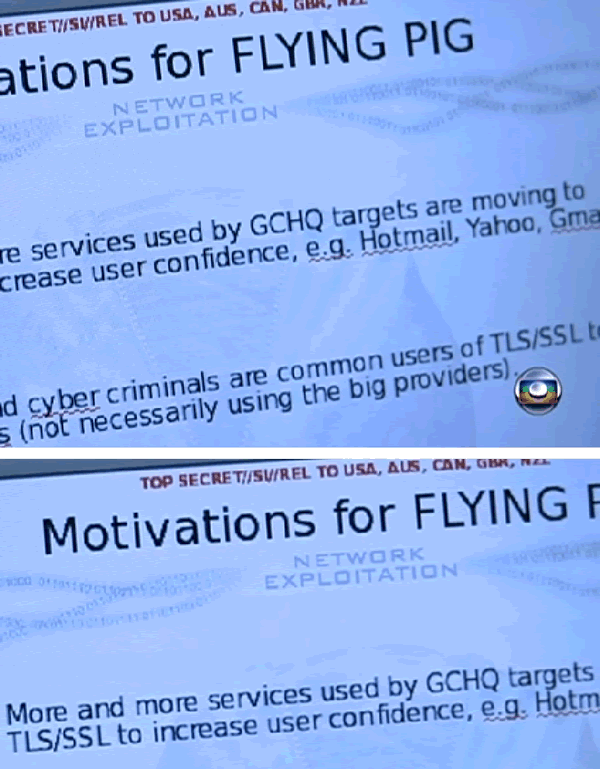
Documents from GCHQ's "network exploitation" unit show that it operates a program called "FLYING PIG" that was started up in response to an increasing use of SSL encryption by email providers like Yahoo, Google, and Hotmail. The FLYING PIG system appears to allow it to identify information related to use of the anonymity browser Tor (it has the option to query "Tor events") and also allows spies to collect information about specific SSL encryption certificates.
Flying Pig Screenshot
Spying on Petrobras - Brazil's Largest Company
Let's take a closer look at NSA Documents Show United States Spied Brazilian Oil Giant
One of the prime targets of American spies in Brazil is far away from the center of power - out at sea, deep beneath the waves. Brazilian oil. The internal computer network of Petrobras, the Brazilian oil giant partly owned by the state, has been under surveillance by the NSA, the National Security Agency of the United States.
These new disclosures contradict statements by the NSA denying espionage for economic purposes.
The information was found by journalist Glen Greenwald, co-author of this story along with TV Globo Reporter Sonia Bridi, amid the thousands of documents given to him by Edward Snowden in June.
This statement addressed to "The Washington Post" this week highlights that 'The department does ***not*** engage in economic espionage in any domain, including cyber.'"
However, a top secret presentation dated May 2012 is used by the NSA to train new agents step-by-step how to access and spy upon private computer networks - the internal networks of companies, governments, financial institutions - networks designed precisely to protect information.
The name of Petrobras - Brazil's largest company - appears right at the beginning, under the title: "MANY TARGETS USE PRIVATE NETWORKS."
The documents are classified as "top-secret", to be seen only by those named by the Americans as "Five Eyes" - the five countries allied in spying: the United States, Australia, Canada, Great Britain and New Zealand.
The name of Petrobras appears on several slides, as the training goes deeper in explaining how date from the target companies is monitored.
Individual folders are created for each target - and contain all the intercepted communications and IP addresses - the identification of each computer on the network - which should be immune to these attacks.
Petrobras has two supercomputers, used mainly for seismic research - which evaluate oil reserves from samples collected at sea. This is how the company mapped the Pre-salt layer, the largest discovery of new oil reserves in the world in recent years.
There is no information on the extent of the spying, nor if it managed to access the data contained in the company's computers. It's clear Petrobras was a target, but no documents show exactly what information the NSA searched for. But at any rate, Petrobras has strategic knowledge of deals involving billions of dollars.
The NSA presentation contains documents prepared by the GCHQ - the British Spy agency, from a country that appears as an ally of the United States in spying. The British agency shows how two spy programs operate. "Flying Pig" and "Hush Puppy" also monitor private networks which carry supposedly secure information. These networks are known as TLS/SSL.
The presentation explains how data is intercepted, through an attack known as "Man in the Middle". In this case, data is rerouted to the NSA central, and then relayed to its destination, without either end noticing.
A few pages ahead, the document lists the results obtained. "Results - what do we find?" "Foreign government networks", "airlines", "energy companies" - like Petrobras - and "financial organisations."
TLS/SSL networks are also the security system used in financial transactions, such as when someone accesses their bank account through an ATM. The connection between a remote terminal and the bank's central goes through a sort of secure tunnel through the internet. No one is supposed to see what travels through it.
Later, the NSA presentation shows in detail how the data of a chosen target is rerouted through spy filters beginning at the very source, until they reach the NSA's supercomputers.
In this document the NSA names Latin America as a key target of the "SILVERZEPHYR" program, which collects the contents of voice recordings, faxes, as well as metadata, which is the overall information being transmitted in the network.
"Flying Pigs", "Hush Puppy", "SILVERZEPHYR"
The NSA was clearly caught lying.
What else besides corporate espionage? Political enemies? (Why not given the target on friends?) State trials? Client attorney privileges?
Once again, I praise Edward Snowden as a national hero for leaking these documents. We would otherwise not know about any of this stuff, and without that leak, it is 100% certain nothing about this would have been done.
Instead, Big Brother would likely have expended to look at every document, every phone call, every corporation, every blog, and literally everything written or said by everyone on the planet, with taxpayers footing the bill.
My fear is that happens regardless.
By Mike "Mish" Shedlock
http://globaleconomicanalysis.blogspot.com
Click Here To Scroll Thru My Recent Post List
Mike Shedlock / Mish is a registered investment advisor representative for SitkaPacific Capital Management . Sitka Pacific is an asset management firm whose goal is strong performance and low volatility, regardless of market direction.
Visit Sitka Pacific's Account Management Page to learn more about wealth management and capital preservation strategies of Sitka Pacific.
I do weekly podcasts every Thursday on HoweStreet and a brief 7 minute segment on Saturday on CKNW AM 980 in Vancouver.
When not writing about stocks or the economy I spends a great deal of time on photography and in the garden. I have over 80 magazine and book cover credits. Some of my Wisconsin and gardening images can be seen at MichaelShedlock.com .
© 2013 Mike Shedlock, All Rights Reserved.
Disclaimer: The above is a matter of opinion provided for general information purposes only and is not intended as investment advice. Information and analysis above are derived from sources and utilising methods believed to be reliable, but we cannot accept responsibility for any losses you may incur as a result of this analysis. Individuals should consult with their personal financial advisors.
Mike Shedlock Archive |
© 2005-2022 http://www.MarketOracle.co.uk - The Market Oracle is a FREE Daily Financial Markets Analysis & Forecasting online publication.



