Peak Freedom - Orwellian CIA Leaking Sieve Vault-7 Hacking Tools Exposed by Wikileaks
Politics / Intelligence Agencies Mar 08, 2017 - 01:48 AM GMTBy: Nadeem_Walayat
 President Trump recently stated that he loves Wikileaks, predominantly in response to its leaking of Hillary Clinton's emails. And in that spirit Wikileaks latest leak of near 9000 CIA documents once more reminds all the extent to which the NSA and CIA wish to eavesdrop into the lives of potentially every person on the planet, friend or foe does not matter for the CIA seeks to surveil everyone and everything through hacking of a myriad of internet connected devices from Android and Apple smartphone's to Samsung smart TV's, to the more traditional PC's infected with malware and web cam hacking routes. ALL used to surveil, record, catalog and process near infinite amounts of data across a network of huge data centres that have sprung up across remote areas of the United States during the past 15 years that tap into an estimated 98.6% of the worlds internet traffic generated by web connected devices.
President Trump recently stated that he loves Wikileaks, predominantly in response to its leaking of Hillary Clinton's emails. And in that spirit Wikileaks latest leak of near 9000 CIA documents once more reminds all the extent to which the NSA and CIA wish to eavesdrop into the lives of potentially every person on the planet, friend or foe does not matter for the CIA seeks to surveil everyone and everything through hacking of a myriad of internet connected devices from Android and Apple smartphone's to Samsung smart TV's, to the more traditional PC's infected with malware and web cam hacking routes. ALL used to surveil, record, catalog and process near infinite amounts of data across a network of huge data centres that have sprung up across remote areas of the United States during the past 15 years that tap into an estimated 98.6% of the worlds internet traffic generated by web connected devices.
 Wikileaks Exposure of CIA Vault-7 Hacking Tools for total Surveillance:
Wikileaks Exposure of CIA Vault-7 Hacking Tools for total Surveillance:
7 March 2017, WikiLeaks begins its new series of leaks on the U.S. Central Intelligence Agency. Code-named "Vault 7" by WikiLeaks, it is the largest ever publication of confidential documents on the agency.
The first full part of the series, "Year Zero", comprises 8,761 documents and files from an isolated, high-security network situated inside the CIA's Center for Cyber Intelligence in Langley, Virgina. It follows an introductory disclosure last month of CIA targeting French political parties and candidates in the lead up to the 2012 presidential election.
Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized "zero day" exploits, malware remote control systems and associated documentation. This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.
"Year Zero" introduces the scope and direction of the CIA's global covert hacking program, its malware arsenal and dozens of "zero day" weaponized exploits against a wide range of U.S. and European company products, include Apple's iPhone, Google's Android and Microsoft's Windows and even Samsung TVs, which are turned into covert microphones.
Since 2001 the CIA has gained political and budgetary preeminence over the U.S. National Security Agency (NSA). The CIA found itself building not just its now infamous drone fleet, but a very different type of covert, globe-spanning force — its own substantial fleet of hackers. The agency's hacking division freed it from having to disclose its often controversial operations to the NSA (its primary bureaucratic rival) in order to draw on the NSA's hacking capacities.
By the end of 2016, the CIA's hacking division, which formally falls under the agency's Center for Cyber Intelligence (CCI), had over 5000 registered users and had produced more than a thousand hacking systems, trojans, viruses, and other "weaponized" malware. Such is the scale of the CIA's undertaking that by 2016, its hackers had utilized more code than that used to run Facebook. The CIA had created, in effect, its "own NSA" with even less accountability and without publicly answering the question as to whether such a massive budgetary spend on duplicating the capacities of a rival agency could be justified.
CIA malware targets iPhone, Android, smart TVs
CIA malware and hacking tools are built by EDG (Engineering Development Group), a software development group within CCI (Center for Cyber Intelligence), a department belonging to the CIA's DDI (Directorate for Digital Innovation). The DDI is one of the five major directorates of the CIA (see this organizational chart of the CIA for more details).
The EDG is responsible for the development, testing and operational support of all backdoors, exploits, malicious payloads, trojans, viruses and any other kind of malware used by the CIA in its covert operations world-wide.
The increasing sophistication of surveillance techniques has drawn comparisons with George Orwell's 1984, but "Weeping Angel", developed by the CIA's Embedded Devices Branch (EDB), which infests smart TVs, transforming them into covert microphones, is surely its most emblematic realization.
The attack against Samsung smart TVs was developed in cooperation with the United Kingdom's MI5/BTSS. After infestation, Weeping Angel places the target TV in a 'Fake-Off' mode, so that the owner falsely believes the TV is off when it is on. In 'Fake-Off' mode the TV operates as a bug, recording conversations in the room and sending them over the Internet to a covert CIA server.
As of October 2014 the CIA was also looking at infecting the vehicle control systems used by modern cars and trucks. The purpose of such control is not specified, but it would permit the CIA to engage in nearly undetectable assassinations.
CIA malware targets Windows, OSx, Linux, routers
The CIA also runs a very substantial effort to infect and control Microsoft Windows users with its malware. This includes multiple local and remote weaponized "zero days", air gap jumping viruses such as "Hammer Drill" which infects software distributed on CD/DVDs, infectors for removable media such as USBs, systems to hide data in images or in covert disk areas ( "Brutal Kangaroo") and to keep its malware infestations going.
Many of these infection efforts are pulled together by the CIA's Automated Implant Branch (AIB), which has developed several attack systems for automated infestation and control of CIA malware, such as "Assassin" and "Medusa".
Attacks against Internet infrastructure and webservers are developed by the CIA's Network Devices Branch (NDB).
The CIA has developed automated multi-platform malware attack and control systems covering Windows, Mac OS X, Solaris, Linux and more, such as EDB's "HIVE" and the related "Cutthroat" and "Swindle" tools, which are described in the examples section below.
Evading forensics and anti-virus
A series of standards lay out CIA malware infestation patterns which are likely to assist forensic crime scene investigators as well as Apple, Microsoft, Google, Samsung, Nokia, Blackberry, Siemens and anti-virus companies attribute and defend against attacks.
"Tradecraft DO's and DON'Ts" contains CIA rules on how its malware should be written to avoid fingerprints implicating the "CIA, US government, or its witting partner companies" in "forensic review". Similar secret standards cover the use of encryption to hide CIA hacker and malware communication (pdf), describing targets & exfiltrated data (pdf) as well as executing payloads (pdf) and persisting (pdf) in the target's machines over time.CIA hackers developed successful attacks against most well known anti-virus programs. These are documented in AV defeats, Personal Security Products, Detecting and defeating PSPs and PSP/Debugger/RE Avoidance. For example, Comodo was defeated by CIA malware placing itself in the Window's "Recycle Bin". While Comodo 6.x has a "Gaping Hole of DOOM".
CIA hackers discussed what the NSA's "Equation Group" hackers did wrong and how the CIA's malware makers could avoid similar exposure.
UMBRAGE
The CIA's hand crafted hacking techniques pose a problem for the agency. Each technique it has created forms a "fingerprint" that can be used by forensic investigators to attribute multiple different attacks to the same entity.
This is analogous to finding the same distinctive knife wound on multiple separate murder victims. The unique wounding style creates suspicion that a single murderer is responsible. As soon one murder in the set is solved then the other murders also find likely attribution.
The CIA's Remote Devices Branch's UMBRAGE group collects and maintains a substantial library of attack techniques 'stolen' from malware produced in other states including the Russian Federation.
With UMBRAGE and related projects the CIA cannot only increase its total number of attack types but also misdirect attribution by leaving behind the "fingerprints" of the groups that the attack techniques were stolen from.
UMBRAGE components cover keyloggers, password collection, webcam capture, data destruction, persistence, privilege escalation, stealth, anti-virus (PSP) avoidance and survey techniques.
Fine Dining
Fine Dining comes with a standardized questionnaire i.e menu that CIA case officers fill out. The questionnaire is used by the agency's OSB (Operational Support Branch) to transform the requests of case officers into technical requirements for hacking attacks (typically "exfiltrating" information from computer systems) for specific operations. The questionnaire allows the OSB to identify how to adapt existing tools for the operation, and communicate this to CIA malware configuration staff. The OSB functions as the interface between CIA operational staff and the relevant technical support staff.
Among the list of possible targets of the collection are 'Asset', 'Liason Asset', 'System Administrator', 'Foreign Information Operations', 'Foreign Intelligence Agencies' and 'Foreign Government Entities'. Notably absent is any reference to extremists or transnational criminals. The 'Case Officer' is also asked to specify the environment of the target like the type of computer, operating system used, Internet connectivity and installed anti-virus utilities (PSPs) as well as a list of file types to be exfiltrated like Office documents, audio, video, images or custom file types. The 'menu' also asks for information if recurring access to the target is possible and how long unobserved access to the computer can be maintained. This information is used by the CIA's 'JQJIMPROVISE' software (see below) to configure a set of CIA malware suited to the specific needs of an operation.
Improvise (JQJIMPROVISE)
'Improvise' is a toolset for configuration, post-processing, payload setup and execution vector selection for survey/exfiltration tools supporting all major operating systems like Windows (Bartender), MacOS (JukeBox) and Linux (DanceFloor). Its configuration utilities like Margarita allows the NOC (Network Operation Center) to customize tools based on requirements from 'Fine Dining' questionairies.
HIVE is a multi-platform CIA malware suite and its associated control software. The project provides customizable implants for Windows, Solaris, MikroTik (used in internet routers) and Linux platforms and a Listening Post (LP)/Command and Control (C2) infrastructure to communicate with these implants.
The implants are configured to communicate via HTTPS with the webserver of a cover domain; each operation utilizing these implants has a separate cover domain and the infrastructure can handle any number of cover domains.
Whilst wikileaks provides further details of the total surveillance state that the NSA and CIA have been busy constructing, what's new is that the CIA / NSA actually PAY corporations to PRESERVE vulnerabilities in their systems and software, backdoors that the CIA is able to exploit, which means users are permanently exposed to hackers, criminals and other nations. So the CIA is actively PREVENTING CYBER SECURITY IN ITS OWN INTERESTS FOR RETAINING BACKDOOR ACCESS TO SYSTEMS!
In reality we already knew of the total surveillance game that the CIA has been playing for many years, as this reminder of what the intelligence agencies crime syndicate tends to get upto from back in 2013 when Edward Snowden first blew wide open the degree to which the NSA surveils everything and everyone, when they tried to defend themselves by stating that they only collected meta data rather than content which has remained the blanket propaganda response since to the CIA / NSA's full spectrum surveillance programs such as PRISM.
The CIA and NSA's response was to LIE, it's obvious the NSA not only collected meta-data but everything, even back in 2013, for it is quite straightforward for US intelligence agencies to bypass any badly worded Congressional limits to just collating meta-data rather than content as well, which is to use a third party and so in comes Britain's GCHQ, where just one of its surveillance programs TEMPORA involves the UK directly tapping ALL communications across ALL of the 300 or so fibre optic cables that pass through the UK. This content is in totality then made available to the NSA and in fact all US intelligence agencies and virtually all US intelligence contractors (commercial operations) and thereby the NSA subverts Congressional limits for recording meta-data whilst at the same time having full total access to CONTENT as well via GCHQ and other national intelligence agencies such as of Canada and Australia.
For more on how the US intelligence agencies such as the NSA subvert the US constitution then see the following excerpt from my 2013 article -
08 Jun 2013 - Internet is Intelligence Agencies Virtual PRISM for Total State Surveillance And Control
The PRISM system for the all prevailing global phone calls and internet access super surveillance state should not come as any surprise to most readers as new technologies are ALWAYS subverted by the state to spy on its citizens, and so citizens of the world have been given a glimpse into the current state of the surveillance state following leaks of the US operation PRISM which concerns ALL of your private phone calls, transactions, communications, accesses and interactions with virtually all of the major communications and web services from tek giants such as Verizon, AT&T, Google, Microsoft, Amazon, AOL, Yahoo and even Apple, who gave us the anti big brother sales propaganda against IBM near 30 years ago (1984), only now to be revealed that Apple too is part and parcel of the state security apparatus.
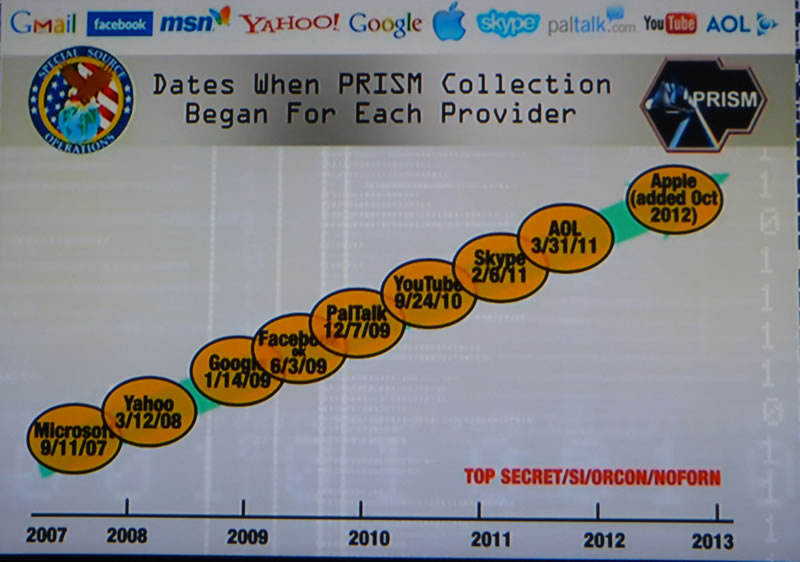

It is increasingly becoming apparent that one of the primary reasons why the internet remains mostly FREE is because it is an excellent tool for not only spying on all aspects of ordinary citizens activities but also on their thought processes which is ultimately what intelligence agencies desire, to control the thought processes of individuals which they aim to seek through conditioning via tools such as the mainstream media, pseudo democracies and state education with further triggers reinforced through individual interactions with state agencies.

The world wide web truly is a web spun by intelligence agencies to capture every aspect of ordinary peoples lives that they seem to share with one another regardless of the consequences to individuals for instance with dictatorships as was the case between documented dealings between MI5 and Gaddaffi and Mubarak's brutal secret police agencies resulting in torture and untold number of deaths.
Meanwhile the CIA and most of the worlds intelligence agencies operate thousands of secret Gulag prisons containing many tens of thousands of political prisoners that the likes of past dictators such as Stalin would be proud of.

As ever Brit's are second class citizens as to the degree to which British people are under state surveillance courtesy not only of the rampant phone and internet surveillance but by far having the most CCTV cameras per capita that the US and Chinese secret police states can only dream of replicating.

The truth as I have often warned of many times during the years is that the intelligence agencies are arms of the elite, and that politicians and democracies are merely fronts for the elite to control as most of the population are taught in state schools to become docile debt slaves in the service of their elite masters. Which my articles have been focused at illuminating the consequences of and strategies for neutralising such as not partaking in the system of debt slavery and being aware of the inflation mega-trend consequences of policies aimed at funneling wealth to the elite, in that individuals can engineer their asset portfolios to be leveraged to inflation as money printing bubbles are repeatedly blown by central banks which is how the elite accumulate their wealth and through which they disenfranchise the mass of the population into owning nothing i.e. people with mortgages own nothing! All mortgage holders are just glorified renters, where if you stop paying the mortgage (rent) then you will be ejected from your home - See Stocks Stealth Bull Market 2013 and Beyond Ebook (FREE DOWNLOAD).
Excerpt from Feb 2011 article.
Britain has All the Infrastructure in Place for a Police State
The dictators of the world can only look on in envy at the surveillance society that exists in Britain, where the movement and activities of Britains 60 million people are constantly tracked and recorded by over 5 million CCTV camera's, approx 15% of the worlds CCTV cameras, utilising facial and car number plate recognition. On top of which there is electronic surveillance of every phone call made and triangulation of mobile phone signals before we even start to introduce personal data generated by internet service providers and easily accessible data-bases on public sites such as Facebook, and state run bureaucracies that document every interaction with the state.
Whilst the Egyptian protests triggered much noise from media whoring politicians and commentators in response to Egyptian Police State tactics such as cutting off of internet access and mobile phone communications between the demonstrators. However the Egyptian regime were mere amateurs when compared to the tactics that the British Police state has deployed against student demonstrators in London over several months, such as the kettling of protestors into an enclosed space for many hours, not allowing anyone to leave so as to break the will of protestors, whilst at the same time selective blocking of mobile communications in specific locations.
The British police have forgotten that they exist to serve the people and not the elite, the current tactics of using video surveillance to identify, track and arrest protestors is akin to totalitarian China than where Britain used to be.
The British police are failing to understand that lawful protest is a fundamental civil right of the people of Britain, that their kettling , provocation, incitement and surveillance tactics are seeking to subvert.
The recent highly public case of under cover police infiltration and incitement operations on climate change activists is further evidence of a defacto police state in action where under cover police officers are inciting protesting groups to break the law. How many more hundreds of under cover police operatives are out there who's primary purpose is to incite a group or protesting crowd into a course of action that they would not have otherwise undertaken so that the police can generate evidence for prosecution.
Therefore contrary to what the British people may assume as to where their personal freedoms stand, Britain is primed to become a police state at literally the flip of a switch, with far more intensive control and interference of the population than the likes of Putin's Russia or Mubarak's Egypt could ever hope to achieve.
The people of Britain need to wake up and realise what is taking place and demand that freedom of speech is both protected and liberated so that the growth of the Police state can be kept in check and the likes of the Russian mafia cancer that is slowly spreading across and out of London can be exposed and neutralised, especially as we have yet to experience the impact of a flood of Chinese Oligarch $billions.
 V
V
I thought we could mark this November the 5th, a day that is sadly no longer remembered, by taking some time out of our daily lives to sit down and have a little chat. There are of course those who do not want us to speak. I suspect even now, orders are being shouted into telephones, and men with guns will soon be on their way. Why? Because while the truncheon may be used in lieu of conversation, words will always retain their power. Words offer the means to meaning, and for those who will listen, the enunciation of truth. And the truth is, there is something terribly wrong with this country, isn't there? Cruelty and injustice, intolerance and oppression. And where once you had the freedom to object, to think and speak as you saw fit, you now have censors and systems of surveillance coercing your conformity and soliciting your submission.
How did this happen? Who's to blame? Well certainly there are those more responsible than others, and they will be held accountable, but again truth be told, if you're looking for the guilty, you need only look into a mirror. I know why you did it. I know you were afraid. Who wouldn't be? War, terror, disease. There were a myriad of problems which conspired to corrupt your reason and rob you of your common sense. Fear got the best of you, and in your panic you turned to the now high chancellor, Adam Sutler. He promised you order, he promised you peace, and all he demanded in return was your silent, obedient consent. Last night I sought to end that silence. Last night I destroyed the Old Bailey, to remind this country of what it has forgotten.
More than four hundred years ago a great citizen wished to embed the fifth of November forever in our memory. His hope was to remind the world that fairness, justice, and freedom are more than words, they are perspectives. So if you've seen nothing, if the crimes of this government remain unknown to you then I would suggest you allow the fifth of November to pass unmarked. But if you see what I see, if you feel as I feel, and if you would seek as I seek, then I ask you to stand beside me one year from tonight, outside the gates of Parliament, and together we shall give them a fifth of November that shall never, ever be forgot.
So the peoples revolution happened during 2016! In Britain and the US, not on November the 5th but on November 8th and June 23rd. However as my article of over 3 years ago clearly illustrates the seeds for BrExit 2016 were sown many, many years ago!
President Trump Understands the Intelligence Agencies LIE
Fast forward to 2017 and we have a skeptical President Trump who pours scorn on the so called intelligence briefings from the CIA and NSA that amount to nothing more than propaganda, the game of mixing just enough truth with fiction so as to present a view in the intelligence agencies own self-interests, self-worth so as to justify further expansion of reach towards total control, towards totalitarian control over the lives of all citizens. Which the people of Britain are fully aware of for we in the UK live actually do live in a police state that just has the trappings of freedom. Tracked from cell tower to cell tower. Meta data that predicts were we will be and with whom through patterns of analysis of for instance our credit and debit card transactions. Which allows subversive agencies to target citizens for instance at their next scheduled supermarket shop, making it relatively easy to engineer state sponsored subversive traps towards neutralising a target who is acting against the interests of the intelligence agencies.

In fact the intelligence agencies do not even need to come anywhere near the target or their residence, for as the CIA leak illustrates that they are able to take full control via remote root access to devices and computers for not just surveillance but for planting of 'evidence' that security apparatus can then act upon.
America is on the same path towards becoming a Police state and what's worse is America's love affair with guns, so a target citizen is infinitely more likely to be assassinated in the United States than the UK which luckily does not have the same history of assassinations of all of whom are deemed to be enemies of the establishment elite, that's potentially 99% of the people. Instead in the UK the name of the game is entrapment and control through state sponsored destruction of lives.
So when Donald Trump tweets :
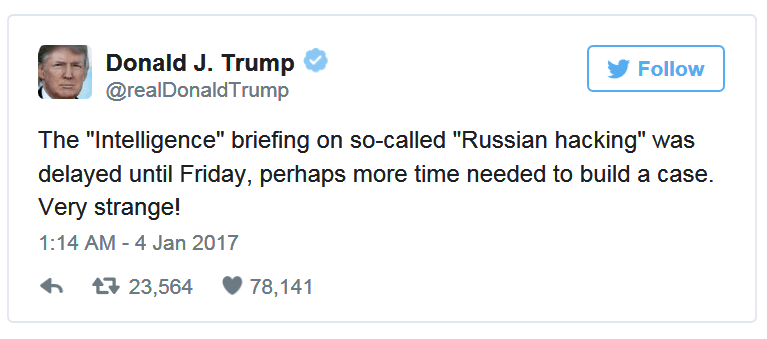
Or tweets alluding to having more faith in wikileaks then the NSA -
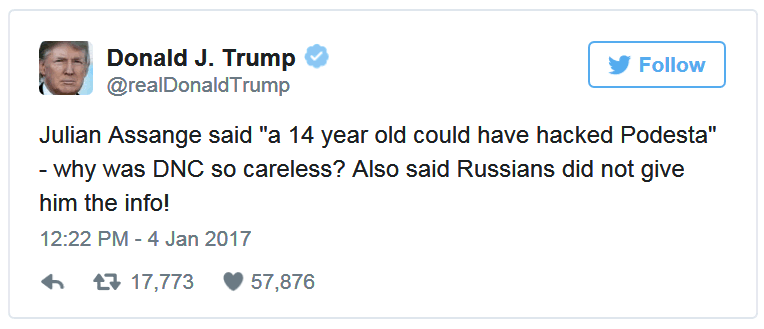
And more recently:
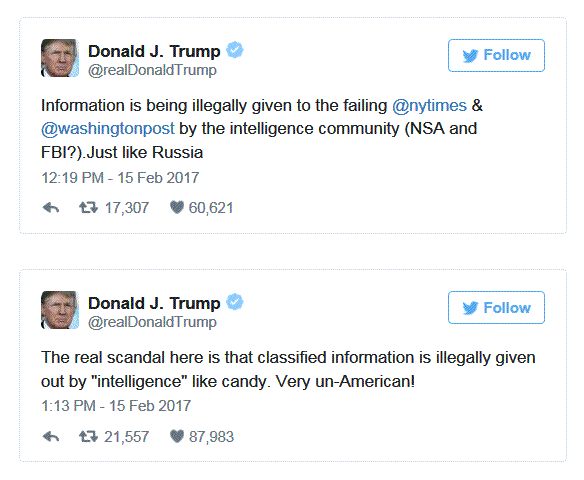
Means is that Trump fully understands the nature of the 'deep state' beast. A beast that is not that distant from the day when it is the NSA and CIA who control the state in totality and not Congress, through FEAR of what they know about everyone! For the truth is that everyone has something to hide, however the full spectrum surveillance coupled with machine intelligence for sifting through the data ensures that every target is neutralised, where the number of targets WILL grow exponentially to encompass everyone from cradle to grave. Control of what people can think are discuss due to the potential consequences from the total surveillance police state.
Whilst the next video explains the nature of the 'deep state' as Mike Lofgren, a congressional staff member for 28 years, talks with Bill Moyers about Washington's "Deep State," in which elected and unelected figures collude to protect and serve powerful vested interests. "It is how we had deregulation, financialization of the economy, the Wall Street bust, the erosion or our civil liberties and perpetual war."
Russia / China Hacking Truth
YES the Russians hack the US. YES China hacks the US. But what the CIA, NSA propagandists fail to mention is that both Russia and China are amateurs when compared to the United States surveillance and hacking programs THAT HACK AND SURVEILLE EVERYONE ON THE PLANET!
So just as US global military power is dominant with both Russia and China boxed in, then so is US Cyber power several magnitudes greater than ALL other nations combined, especially since the intelligence agencies subvert domestic laws by for instance GCHQ hacking the US content for the NSA, which means the NSA has plausible deniability when asked, "do you hack and surveil US citizens?" The answer is always NO, when reality is that they subcontract content theft to GCHQ. And THEFT is what it amounts to, the intelligence agencies operate as a crime syndicate STEALING data, STEALING private information, and organised crime syndicate!
So all we witnessed this week with the heads of the intelligence agencies prancing about Congress was the putting up of a smoke screen for the purposes of -
a. hiding their own criminal activities
b. so as to justify a further expansion of their powers to intrude on the lives of ordinary people.
The bottom line is that the US is trending towards becoming a Police State where the citizens will FEAR the State, for what they know or could know. In fact in many respects we are already there for many people if not most understand that everything they type into for instance Google search is recorded and analysed. Which has the insidious effect of limiting freedom of thought. How can one think freely when one has to be cautious about what one searches for!
The criminal entities that go by the name of the NSA, CIA and dozens more intelligence agencies created by successive governments will not allow anyone, not even a President to question their ever expanding power, authority and reach and thus as I warned in my recent article that there is a real risk that the CIA has plans to assassinate President Donald Trump should be continue on his path of rejecting NSA and CIA authority.
The bottom line is total surveillance PLUS the emergence of artificial intelligence, algorithms able to analyse the vast amounts of data generated each day ensures that western societies have long since passed PEAK FREEDOM and are now well on their way towards becoming police states where people no longer have the freedom to express their thoughts even in private as the omnipresent, all knowing systems of control seek to neutralise any perceived threat to their continuing expansion and total control over every aspect of human life.
UK NEW Cyber Security Headquarters
Whilst in Britain the mainstream press has been busy singing the propaganda praises of Britain's latest addition towards its total surveillance state which in addition to MI5 and MI6, central London now has a new spy agency aiming to employ 700 cyber spies so as to spy on virtually every online activity of the British people whilst the media establishment has been busy throwing up a propaganda smoke screen to mask the facilities true intentions by propagandising its function being one of defending the British people and corporations against cyber crime when instead the EXACT OPPOSITE IS LIKELY TRUE! For just as is the case with the CIA / NSA PAYING corporations to PRESEVE vulnerabilities in their systems so as to allow backdoor access for the CIA, then so will likely be the case for Britain's Cyber Security Headquarter. Thus they will likely be actively PREVENTING CYBER SECURITY which means that the people and corporations of Britain as a consequence of this new facility are likely to now be LESS secure to criminal hacking.

If I was in charge of developing defensive or offensive cyber capabilities then I would NOT be deploying several hundred low tech humans into the field who are really only mostly good for surveilling activities of other humans. Instead I would be concentrating resources on developing self learning AI's that would code and test the defensive and offensive algorithms in machine time, billions of times faster than that which humans are capable of.
So Britains so called Cyber Security headquarters in reality is just the latest extension to Britain's secret police state as a reaction to BREXIT which shocked the establishment elite that never saw it coming, and so this is one of the reactions to BREXIT, the expansion of Britain's total surveillance state under the guise of defending Britain against cyber attack as reported on by the mainstream media.
The bottom line is that the people of Britain need to realise that Britain IS already the worlds most surveilled police state, far beyond anything Czar Putin of Russia could ever hope of replicating, a police state so entrenched and widespread that most people are not even aware of its true size and scope, that following Brexit has gone into over drive in an attempt to maintain the establishments hold over power. However what the elite still fail to realise is this, that the people of Britain, in fact the people of the world have had enough of lying politicians who repeatedly FAIL to do that which they were elected to do! They still don't get it and likely never will! so have gone for their default position which is for the expansion of state security apparatus so as to further control the population rather than realising that the population is no longer willing to put up with the elite playing pass the parcel between themselves at Westminister any longer.
And as for Cyber weapons and cyber wars then unfortunately just as is the case for nuclear weapons there IS NO DEFENCE against state sponsored cyber weapons. NONE. As the 2008 financial crisis illustrated that the worlds financial system is corrupt and unstable and primed for collapse, a collapse which could be triggered by use of cyber weapons the code for which already exists courtesy of the Israeli's weaponizing America's stuxnet code to attack the Iranian nuclear facilities. The Israeli's did not care that the stuxnet virus would spread throughout the world only as long as it reached its intended target, the consequences of which is that now every state has the means to use and work on the stuxnet code developed by the americans and aggressively weaponizing by the Israeli's, which brings cyber financial armageddon several steps closer to being triggered.
So, no there IS no real defence against cyber weapons, where with each version becomes more sophisticated and damaging, and as was the case for nuclear weapons the only real defence is OFFENCE, mutually assured destruction, MAD.
Trump Ramps Up US Military Spending In Preparations for War with China
And where the 'Trump Reset' is concerned, President Trump's recent announcement to request Congress to increase annual US 'defense' spending by $54 billion (10%) to over $650 billion, some ten times that of the likes of Russia or Britain and approximately 40% of total global military spending. Which underscores the reality that there is nothing defensive about the scale of US military spending as the US is a global military empire that far out spends any other nation, where whilst the establishment media makes much of the Russian military threat in reality is a mere smoke and mirrors propaganda exercise as my 'Trump Reset' series of articles illustrates :
28 Dec 2016 - US Empire's Coming Economic, Cyber and Military War With China (Part 2)
Military and Economic Power 2016
| United States | China | India | Russia | UK | Japan | France | Germany | Saudi Arabia | |
| Military Spending | $600bn | $220bn | $50bn | $66bn | $58bn | $45bn | $47bn | $40bn | $85bn |
| Economy | $18.6tr | $11.5tr | $2.25tr | $1.3tr | $2.7tr | $4.7tr | $2.5tr | $3.5tr | $0.65tr |
| Population | 0.33bn | 1.38bn | 1.35bn | 0.145 | 0.065 | 0.127 | 0.065 | 0.082 | 0.033 |
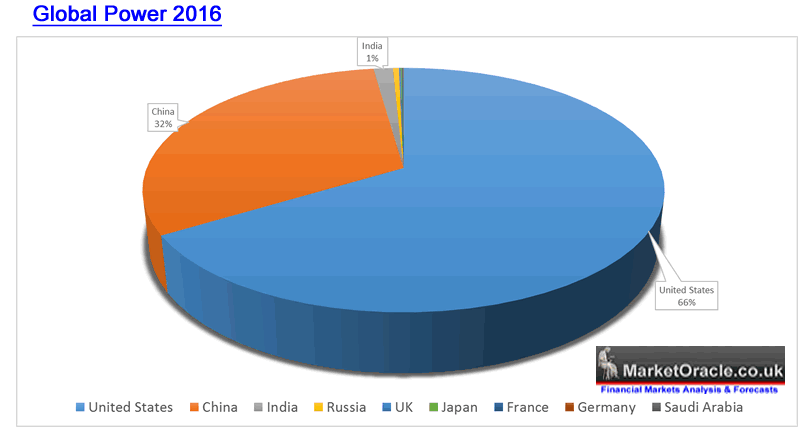
Today, as expected the US ranks No1 in the world, with China 2nd. However whilst in terms of military coupled with economic power Russia may rank fourth in the world today, the gap between the US and China and the rest is such that even the likes of India does not even come close to equating to 3% of the overall capability of the United States as the following global power pie chart better illustrates.
 President Trump proposes that the $54 billion increase in military spending will be financed through unspecified cuts in other federal spending. However, in reality this and further Trump spending proposals and tax cuts will be financed through printing money (government bonds) as the US debt mountain looks set to climb ever higher, soon expanding the current budget deficit of $441 billion to at least $1 trillion per year and by the time Trumps 4 years are up will leave America with a national debt of at least $24 trillion, well over 110% of GDP.
President Trump proposes that the $54 billion increase in military spending will be financed through unspecified cuts in other federal spending. However, in reality this and further Trump spending proposals and tax cuts will be financed through printing money (government bonds) as the US debt mountain looks set to climb ever higher, soon expanding the current budget deficit of $441 billion to at least $1 trillion per year and by the time Trumps 4 years are up will leave America with a national debt of at least $24 trillion, well over 110% of GDP.
Furthermore, My 'Trump Reset' series warned that a Trump Presidency would ultimately be trending towards an outright military conflict with China. Where whilst so far only 3 videos from a planned 14 part series have been published, however the full "Trump Reset - War with China" analysis can be read online in the following 3 articles -
- 27 Dec 2016 - The Trump Reset - Regime Change, Russia the Over Hyped Fake News SuperPower (Part1)
- 28 Dec 2016 - US Empire's Coming Economic, Cyber and Military War With China (Part 2)
- 04 Jan 2017 - CIA Planning Rogue President Donald Trump Assassination? Elites "Manchurian Candidate" Plan B
The Putin Doctrine
My second video concerned Trump following the "Putin Doctrine", one of there being no difference between that which is truth and that which is fiction.
In terms of the capitalising on the expectations for US ramping up defence spending then No 1 on the list of actions to take was / is to invest in the military industrial complex -
28 Dec 2016 - US Empire's Coming Economic, Cyber and Military War With China (Part 2)
FINANCIAL MARKET CONSQUENCES
In terms of the financial markets i.e. profiting from the new cold war with China then there are five key implications:
1. MILITARY INDUSTRIAL COMPLEX INVESTING - Investing in the western defence and the military industrial complex as the US and other Asian nation’s ramp up defence spending too far out match that of China's growing defence budget as Trump's statements implied would be required of Asian allies.
"You know we have a treaty with Japan, where if Japan is attacked, we have to use the full force and might of the United States". "If we're attacked, Japan doesn't have to do anything. They can sit home and watch Sony television."
"They're paying us a tiny fraction of what it's costing. I'd love to continue to defend Japan, I'd love to continue to defend South Korea - we have 28,000 soldiers on the line between North and South Korea right now. It's costing us a fortune, which we don't have, we're a debtor nation,"
Whilst European nation are also expected to increase defence spending to counter the perceived (over blown) Russian threat as the US withdraws and redirects its military forces increasingly towards the containment and suppression of China. China is NOT going to be allowed the chance to become the next Soviet Union.
Ensure you are subscribed to my always free newsletter and youtube channel for forthcoming analysis and detailed trend forecasts aimed at capitalising on the Trump Reset.
Source and comments : http://www.marketoracle.co.uk/Article58369.html
By Nadeem Walayat
Copyright © 2005-2017 Marketoracle.co.uk (Market Oracle Ltd). All rights reserved.
Nadeem Walayat has over 25 years experience of trading derivatives, portfolio management and analysing the financial markets, including one of few who both anticipated and Beat the 1987 Crash. Nadeem's forward looking analysis focuses on UK inflation, economy, interest rates and housing market. He is the author of five ebook's in the The Inflation Mega-Trend and Stocks Stealth Bull Market series that can be downloaded for Free.
 Nadeem is the Editor of The Market Oracle, a FREE Daily Financial Markets Analysis & Forecasting online publication that presents in-depth analysis from over 1000 experienced analysts on a range of views of the probable direction of the financial markets, thus enabling our readers to arrive at an informed opinion on future market direction. http://www.marketoracle.co.uk
Nadeem is the Editor of The Market Oracle, a FREE Daily Financial Markets Analysis & Forecasting online publication that presents in-depth analysis from over 1000 experienced analysts on a range of views of the probable direction of the financial markets, thus enabling our readers to arrive at an informed opinion on future market direction. http://www.marketoracle.co.uk
Disclaimer: The above is a matter of opinion provided for general information purposes only and is not intended as investment advice. Information and analysis above are derived from sources and utilising methods believed to be reliable, but we cannot accept responsibility for any trading losses you may incur as a result of this analysis. Individuals should consult with their personal financial advisors before engaging in any trading activities.
Nadeem Walayat Archive |
© 2005-2022 http://www.MarketOracle.co.uk - The Market Oracle is a FREE Daily Financial Markets Analysis & Forecasting online publication.